According to ETH Zurich researchers Sandro Rüegge, Johannes Wikner, and Kaveh Razavi, Spectre v2 mitigations held for six long years, but their new "Branch Predictor Race Conditions" exploit casually steamrolls them.
The mess, named ‘branch privilege injection’ and filed under CVE-2024-45332, is a race condition in Intel’s beloved branch predictors, namely the Branch Target Buffer (BTB) and Indirect Branch Predictor (IBP).
These guess-happy bits of silicon predict branch outcomes to keep Intel's creaky pipelines chugging along, but ETH Zurich found their updates are not synchronised with instruction execution. This allows speculative updates to waltz merrily across privilege boundaries.
When privilege switches happen, like jumping from user mode to kernel mode, there is a tiny window where updates carry the wrong privilege baggage. The result: isolation between user and kernel is toast.
The researchers cooked up an exploit that trains the CPU to expect a specific branch, then fires a system call to trigger speculative execution in the kernel with an attacker-controlled "gadget". This leaks secret data into the cache, where side-channel snooping picks it up like loose change from a sofa.
ETH Zurich's team proved it on Ubuntu 24.04, reading from the ‘/etc/shadow/’ file containing password hashes. They clocked peak leak rates of 5.6 KB/sec with a depressing 99.8 per cent accuracy.
All Intel processors from Coffee Lake Refresh (ninth generation) onwards are riddled with this, including Comet Lake, Rocket Lake, Alder Lake, and Raptor Lake.
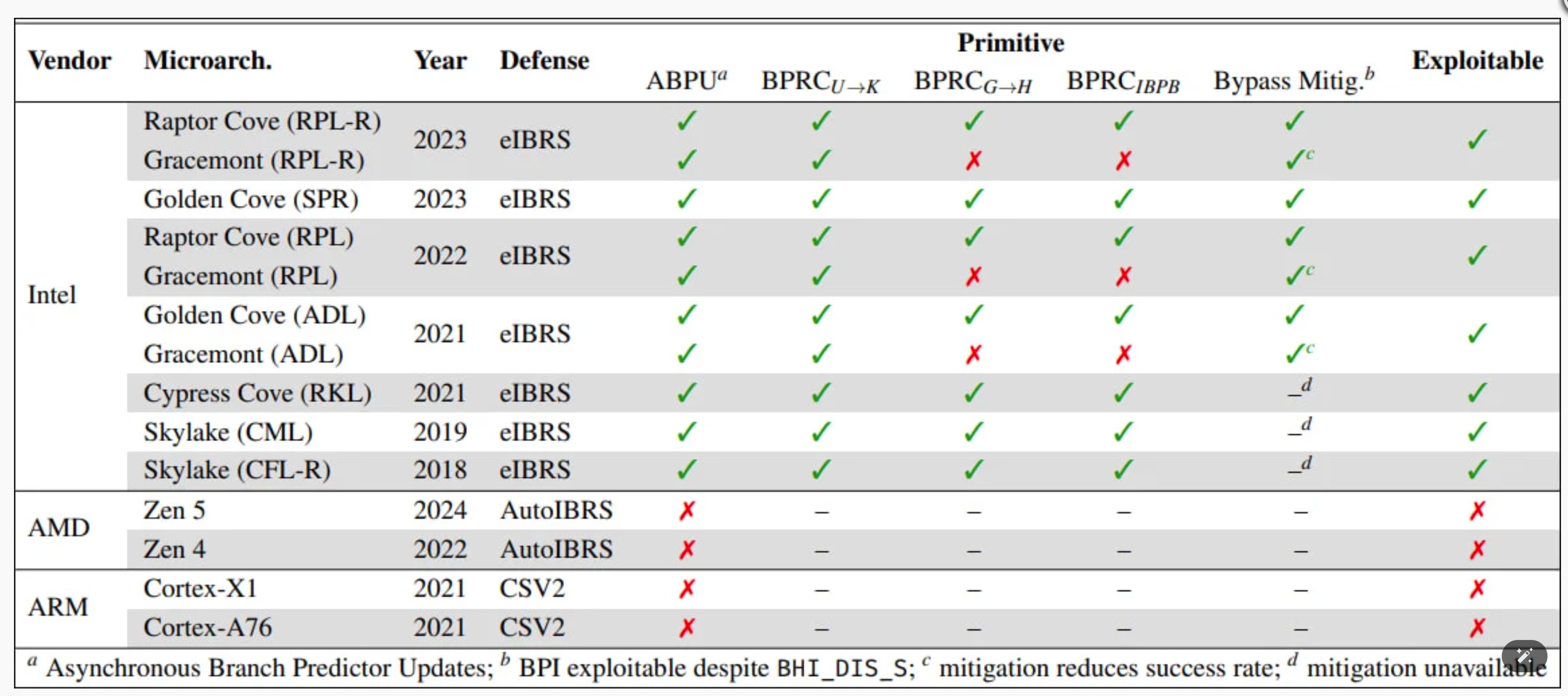
ETH Zurich warned, "All Intel processors since the 9th generation (Coffee Lake Refresh) are affected by Branch Privilege Injection," although mispredictions were spotted on Kaby Lake chips too.
Older CPUs might dodge this particular bullet but are probably even more vulnerable to other Spectre-style disasters. Meanwhile, Arm and AMD dodged this one by designing something that does not, apparently, suck quite as badly. Although the exploit was shown off on Linux, it is baked into the silicon, so Windows boxes are just as tasty a target.
Chipzilla was tipped off in September 2024 and dribbled out some microcode updates to patch the flaw. The firmware fix brings a 2.7 per cent performance hit, while software bodges range from 1.6 to 8.3 per cent, depending how optimistic you are.
Intel’s spin doctors said: “We appreciate the work done by ETH Zurich on this research and collaboration on coordinated public disclosure. Intel is strengthening its Spectre v2 hardware mitigations and recommends customers contact their system manufacturer for the appropriate update. To date, Intel is not aware of any real-world exploits of transient execution vulnerabilities.”
In other words, move along, nothing to see here. ETH Zurich will drop the full technical horror show at USENIX Security 2025.




